|
| |
 |
Released by :
tlr
Release Date :
24 February 2008
Type :
C64 Misc.
|
Credits :
Download :
Look for downloads on external sites:
Pokefinder.org
User Comment
Submitted by Mantiz on 24 February 2008
I saw it was 16 chars so I assumed 128 bit encryption. After that, with the hint in mind, looking up a few possible passwords for that did not take long. I've looked at the code and I think cracking this password with another method would take significantly longer time than this. A brute force approach other than a dictionary one would not be possible in a reasonable timeframe. I don't see how you could solve this even if you know the algorithm without the key.
Keep them coming, great fun :) |
User Comment
Submitted by tlr on 24 February 2008
| Thanks for the positive comments! :) |
User Comment
Submitted by Wisdom on 24 February 2008
| tlr, congratulations for taking such interesting and definitely not trivial challenges! First the statistical solver and now this AES decrypter. Deep respect! |
User Comment
Submitted by tlr on 24 February 2008
I think most guessed it.
Ymgve googled for the first values of the S-Box at $c000, which was quite clever.
Added full source code. |
User Comment
Submitted by Quetzal on 24 February 2008
Nice work! Thanks for posting the answer, since I was going mad trying to crack it. How did others manage to work it out? Or were they all guesses/tipped off by recognizing the algorithm?
Now I'll have to set to work on the conversion of Twofish so that 64 users will have another choice available in strong encryption. :)
|
User Comment
Submitted by MagerValp on 24 February 2008
| Excellent, now please post the source :) |
User Comment
Submitted by tlr on 24 February 2008
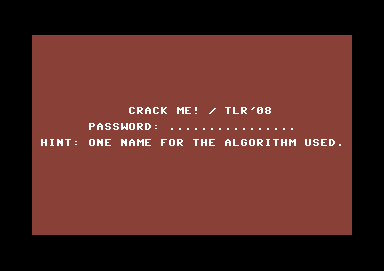
Password: "RIJNDAEL"
The program is encrypted using AES-128 running in Electronic Code Book mode.
As you may know AES-128 is a subset of Rijndael.
Solved by:
1. Mantiz
2. Ymgve
3. MagerValp
4. Unseen
Apparently the hint was too obvious for some.
Maybe I'll make a harder one. :)
|
User Comment
Submitted by MagerValp on 24 February 2008
User Comment
Submitted by tlr on 23 February 2008
| Magervalp and Unseen has cracked it too now. |
User Comment
Submitted by tlr on 23 February 2008
I've gotten two correct answers so far.
Mantiz was first. :)
It's interesting to hear the explanations on how the pw was found, keep them coming! :) |
User Comment
Submitted by Ymgve on 23 February 2008
User Comment
Submitted by tlr on 23 February 2008
Let's just say it's a bonus. :)
It does what most file coders on the c64 does, i.e decrypts, and then does RUN on the result.
Trying to check the key for validity often results in weakening the encryption and therefore should be avoided. |
User Comment
Submitted by LordNikon on 23 February 2008
| hehe, nice way to say that the pw is wrong :) |
User Comment
Submitted by tlr on 23 February 2008
That means you've got the wrong pw... :)
|
User Comment
Submitted by LordNikon on 23 February 2008
User Comment
Submitted by tlr on 23 February 2008
I challenge you to crack the code! ;)
PM me first when you find it so I can announce the winner. :) |
|
|
|
 | Search CSDb |
|
 | Navigate |  |
|
 | Detailed Info |  |
|
 | Fun Stuff |  |
· Goofs
· Hidden Parts
· Trivia
|
|
 | Forum |  |
|
 | Support CSDb |  |
|
 |  |
|


