|
| |
|
Bleepload Transfer Alpha 1.0 [2015] |
Credits :
Download :
Look for downloads on external sites:
Pokefinder.org
Summary
Submitted by Fungus on 5 August 2015
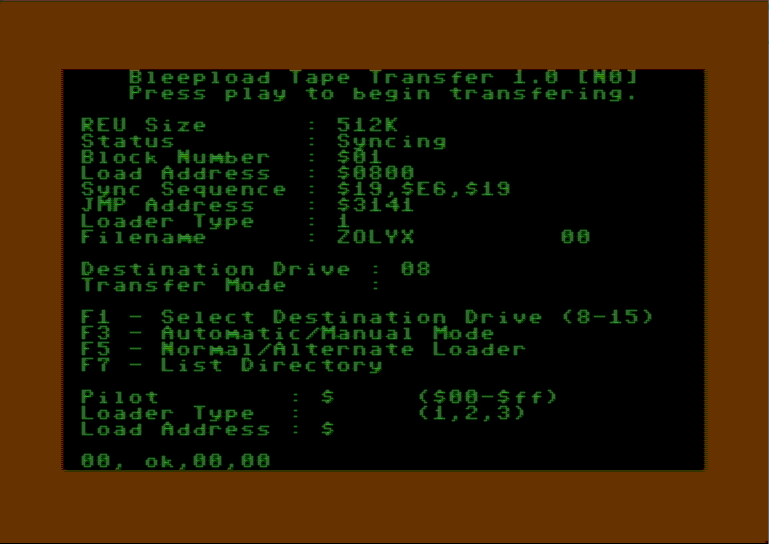
This is a proof of concept for a generic bleepload transfer utility utilizing an REU. I took it as a challenge as it was said that it
is "impossible" to make an automatic transfer for this particular protection that runs on a c64. Right ;)
Unfortunately I lost the drive to finish it, it's about 70% complete and can transfer files as well as decrypt the start block.
I didn't finish the auto scanning for the 2 types of loader, or the pilot/load address scanner. I don't remember if I finished the type 2 loader either.
I also planned to have a manual mode in case the scanner failed so you could still use it to transfer the files on a tape that was not
conforming to what I have already reverse engineered.
It loads and decrypts the files and saves them to disk, it also saves the jmp tables to a separate file so you can examine the calls to any
picture displayer or the main entry point.
Anyways I thought I would share it with the world in case anyone wanted to finish it. The tool chain is tass64, exomizer and c1541.
I tried to keep all the routines generic and utlitarian so that they can be easily adapted to other transfers with minimal work.
The code is well commented, so it should be easy enough to figure it out. I did not get around to splitting it up into smaller chunks, sorry.
The "to do list" is in the code comments.
I've included my notes on reverse engineering and disassemblies of the loader variants, and the entry point code. Luigi DiFraia must be credited
for the initial work on documenting the bleepload binary format.
If you want to finish it, or make your own based on the concepts, please do. I would ask that you acknowledge the work I put into this.
- Fungus |
|
|
|
 | Search CSDb |
|
 | Navigate |  |
|
 | Detailed Info |  |
|
 | Fun Stuff |  |
· Goofs
· Hidden Parts
· Trivia
|
|
 | Forum |  |
|
 | Support CSDb |  |
|
 |  |
|